MySQL Sandbox 3.1.07 adds several options to execute shell or SQL commands during the sandbox installation.
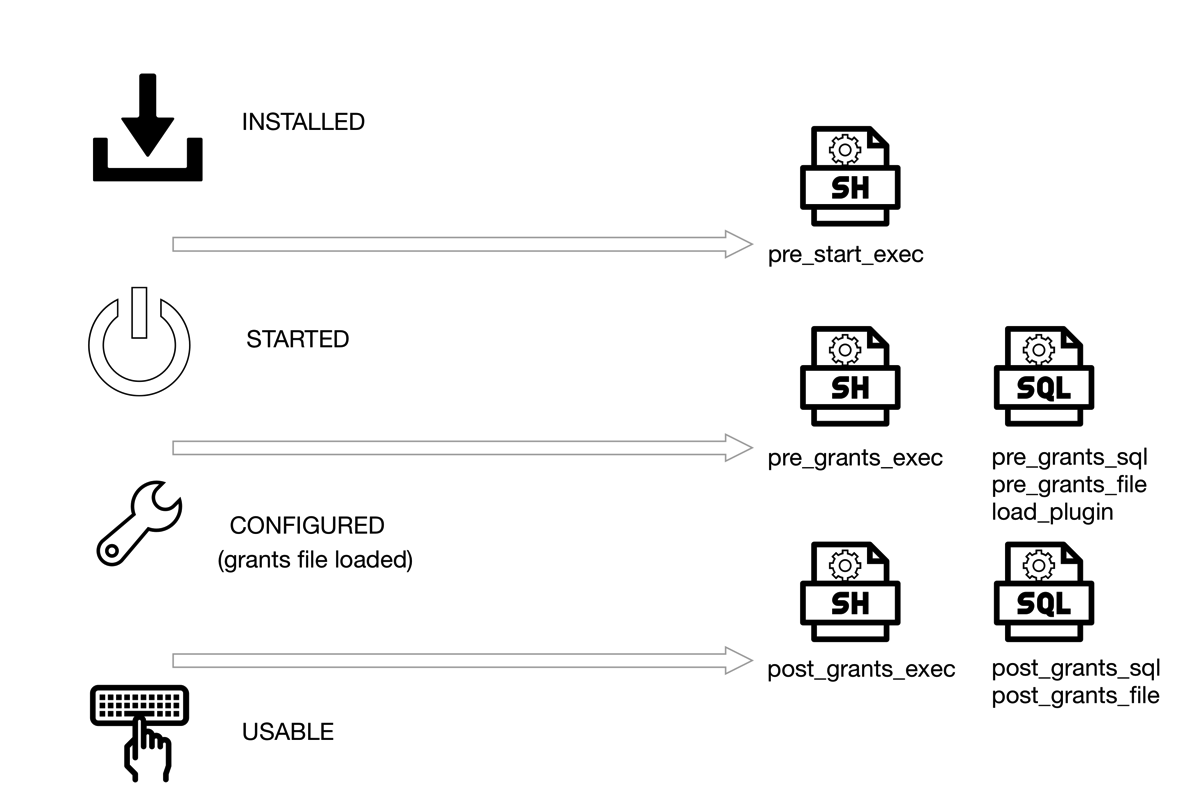
Figure 1: MySQL Sandbox states and where you can run the hooks
There are 3 options to run shell commands, 2 to run SQL queries, and 2 to run SQL files.
## Shell commands
--pre_start_exec=command : runs 'command' after the installation, before the server starts
--pre_grants_exec=command : runs 'command' after the server starts, before loading the grants.
--post_grants_exec=command : runs 'command' after the loading the grants.
## SQL statements
--pre_grants_sql=query : runs 'query' before loading the grants.
--pre_grants_file=filename : runs SQL file 'filename' before loading the grants.
--post_grants_sql=query : runs 'query' after the loading the grants.
--post_grants_file=filename : runs SQL file 'filename' before loading the grants.
Moreover, a new option --load_plugin=plugin[:plugin_file_name] loads a given plugin before the grants file is loaded.
What can you use this for?
The need arose when I needed general log activated at start-up, but did not want the option to stay in the configuration file. Then I also found that running a SQL command to install a plugin and check its status would be nice to have. When enough cases piled up, I implemented a few changes that allow MySQL Sandbox to accept commands at specific stages of the deployment. Figure 1 shows where these hooks are available.
Some use cases for SQL:
- activate general log;
- install plugins (although there is a specialized option for that)
- enable superreadonly : this will only work after loading grants. If enabled before, the user creation commands will fail.
- show the status of database variables, status, and objects.
Some use case for shell commands:
- See the composition of the sandbox at various stages;
- Run diagnostic tools, backups, synchronization tasks;
- Perform dangerous tasks to test the server responsiveness;
- General purpose hacks.
When the shell command runs, MySQL Sandbox provides several environment variables that facilitate interaction with the database that has been installed.
SANDBOX_DIR = sandbox directory;
BASEDIR = base directory for the sandbox binaries
DB_DATADIR = data directory
MY_CNF = configuration file
DB_PORT = database port
DB_USER = database user
DB_PASSWORD = database password
DB_SOCKET = database socket
MYSQL_VERSION = MySQL version (e.g. 5.7.12)
MYSQL_MAJOR = Major part of the version (e.g 5)
MYSQL_MINOR = Minor part of the version (e.g 7)
MYSQL_REV = Revision part of the version (e.g 12)
EXEC_STAGE = Stage of the execution (pre_start_exec, pre_grants_exec, post_grants_exec)
Figure 2: MySQL Sandbox order of execution
You can combine shell and SQL calls for all stages. They will run in the order shown in Figure 2.
Examples
Let's install the XPlugin. And using the shell commands we can check the status of the system from the outside.
$ make_sandbox 5.7.12 -- --load_plugin=mysqlx \
--pre_grants_exec='echo "##open ports";sudo netstat -atn |grep LISTEN|grep 33060; echo "##"' \
--post_grants_exec='echo "open ports";sudo netstat -atn |grep LISTEN|grep 33060;echo "##"'
[...]
# Starting server
.. sandbox server started
# [pre_grants_exec] system "echo "##open ports";sudo netstat -atn |grep LISTEN|grep 33060; echo "##""
##open ports
##
--------------
INSTALL PLUGIN mysqlx soname 'mysqlx.so'
--------------
--------------
select plugin_name, plugin_version, plugin_status from information_schema.plugins where plugin_name = 'mysqlx'
--------------
+-------------+----------------+---------------+
| plugin_name | plugin_version | plugin_status |
+-------------+----------------+---------------+
| mysqlx | 1.0 | ACTIVE |
+-------------+----------------+---------------+
# Loading grants
# [post_grants_exec] system "echo "open ports";sudo netstat -atn |grep LISTEN|grep 33060;echo "##""
open ports
tcp4 0 0 *.33060 *.* LISTEN
##
Your sandbox server was installed in $HOME/sandboxes/msb_5_7_12
Here, the load_plugin option loads the plugin before the grants. Before this happens, the shell command runs netstat to check the status of port 33060, which is the one that the MySQL XProtocol uses by default. We can see that the port is not available at that stage. The same command running after the grants are loaded shows that the port is open.
Another example. This time we will use a shell script that uses most of the variables listed above:
$ cat t/test_init_exec.sh
#!/bin/bash
echo "----------------------------------------------------------------"
echo "Stage: $EXEC_STAGE"
if [ "$EXEC_STAGE" == "pre_start_exec" ]
then
echo "PWD <$PWD> "
echo "VER <$MYSQL_VERSION> "
echo "DIR <$SANDBOX_DIR> "
echo "DATADIR <$DB_DATADIR> "
echo "BASEDIR <$BASEDIR> "
echo "SOCKET <$DB_SOCKET> "
echo "MY_CNF <$MY_CNF>"
echo "USER/PASSWORD/PORT <$DB_USER> <$DB_PASSWORD> <$DB_PORT> "
echo "Version components <$MYSQL_MAJOR> <$MYSQL_MINOR> <$MYSQL_REV>"
fi
cd $SANDBOX_DIR
# ls
echo '## Data directory'
ls data
echo "----------------------------------------------------------------"
The script shows the value of the variables for the first stage only and the contents of the data directory:
$ make_sandbox 5.7.12 -- --pre_start_exec=./t/test_init_exec.sh --post_grants_exec=./t/test_init_exec.sh
[...]
# [pre_start_exec] system "./t/test_init_exec.sh"
----------------------------------------------------------------
Stage: pre_start_exec
PWD <$HOME/workdir/git/mysql-sandbox>
VER <5.7.12>
DIR <$HOME/sandboxes/msb_5_7_12>
DATADIR </Users/gmax/sandboxes/msb_5_7_12/data>
BASEDIR <$HOME/opt/mysql/5.7.12>
SOCKET </tmp/mysql_sandbox5712.sock>
MY_CNF <$HOME/sandboxes/msb_5_7_12/my.sandbox.cnf>
USER/PASSWORD/PORT <msandbox> <msandbox> <5712>
Version components <5> <7> <12>
## Data directory
auto.cnf ib_buffer_pool ibdata1 mysql performance_schema sys
----------------------------------------------------------------
# Starting server
.. sandbox server started
# Loading grants
# [post_grants_exec] system "./t/test_init_exec.sh"
----------------------------------------------------------------
Stage: post_grants_exec
## Data directory
auto.cnf ib_logfile0 ibdata1 msandbox.err mysql_sandbox5712.pid performance_schema test
ib_buffer_pool ib_logfile1 ibtmp1 mysql mysqld_safe.pid sys
----------------------------------------------------------------
Your sandbox server was installed in $HOME/sandboxes/msb_5_7_12
We can see that the data directory, before the server starts, contains only the files created by mysqld --initialize-insecure, while after the start and the grant load we get the InnoDB log files, the .pid files, and the test database (created by the grants script).





No comments:
Post a Comment